Misconfigured C&C Server
Hi to everyone,
tonight We talk about how to make difficult the cybercriminal's illegal job.
Everything starts from www.hybrid-analysis.com; where I had the opportunity to quickly analyze a Loki sample.
From a network analysis I was able to identify the Loki Web Panel aka LokiPWS.
Furthermore the malicious Web Server under analysis presents a Directory Indexing

so I was easily able to identify five differents web panels that we will call with some nicknames:
a0/ --> LokiPWS: no weak password
a1/ --> LokiPWS: weak password
a2/ --> Pony 2.0 Web Panel: no weak password
a3/ --> LokiPWS: weak password
a4/ --> Bilal Ghouri PHP: weak password
Following, the github/pastebin links that helped me during this article:
Loki PWS
Pony 2.0
Bilal Ghouri PHP
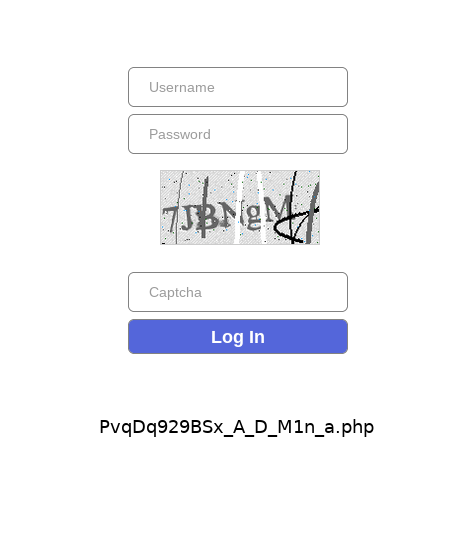
Starting from a1 an empty page was shown, but from the previously mentioned links I was able to identify the login page at PvqDq929BSx_A_D_M1n_a.php
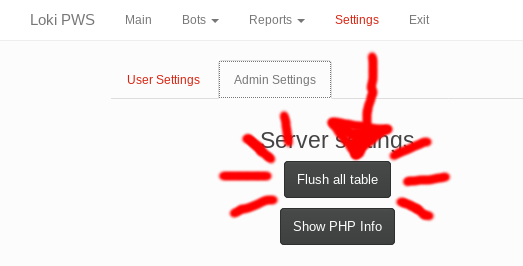
And obviously the next step was to clear all the collected/stealed credentials and bots:
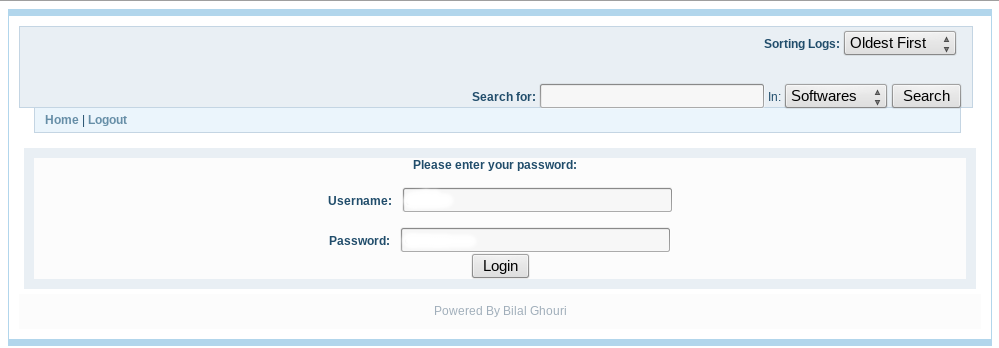
Next it was the turn of a4/
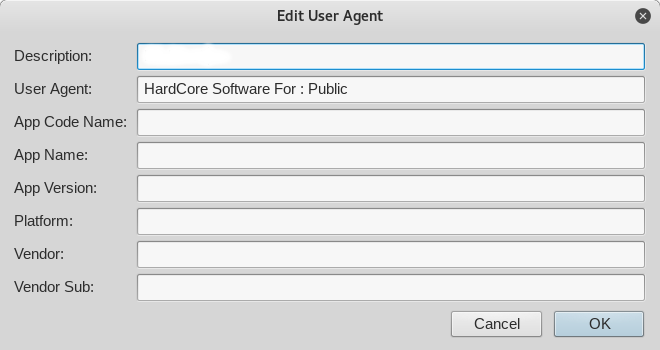
Analyzing the source code founded on pastebin, I was able to identify a Stored XSS, which we could exploit following these steps:
1) Change User-Agent to "HardCore Software For : Public" (looking at "define(USER_AGENT, 'HardCore Software For : Public');")
2) Call "a4/?action=add&app=%3Cimg%20src=x%20onerror=alert(1)%3E&username=&sitename=&password=&pcname="
And here the result:
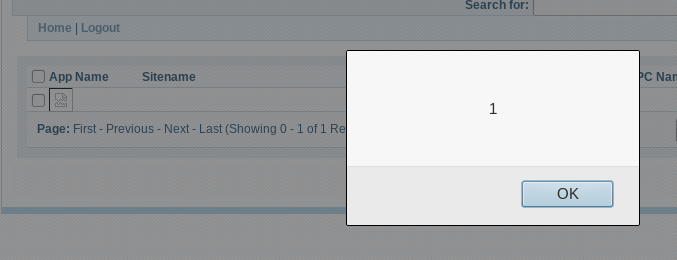
I want to underline that doing illegal actions is a crime; but from my point of view also act as if We hasn't viewed, is a crime.
So I felt compelled to delete the data collected by the criminal and also to scare him with a stupid "alert(1)".
See you soon.