Application InSecurity: Hide Folders 2.5
Hi to everyone,
today We talk about some Reverse Engineering fun.
The target application will be Hide Folders 2.5 for Windows 32bit.
As the developer says on his website ( http://www.hidefolders.org/ ):
"Hide Folders allows you to securely hide folders with your private and sensitive data."
What if you have forgot the password to "unhide" directories?
Let's start our Win32 Debugger like Ollydbg or Immunity Debugger and attach to the application.
After typing the bad password the MessageBox with text "Wrong Password" appear.
So first of all let's search the ascii string:
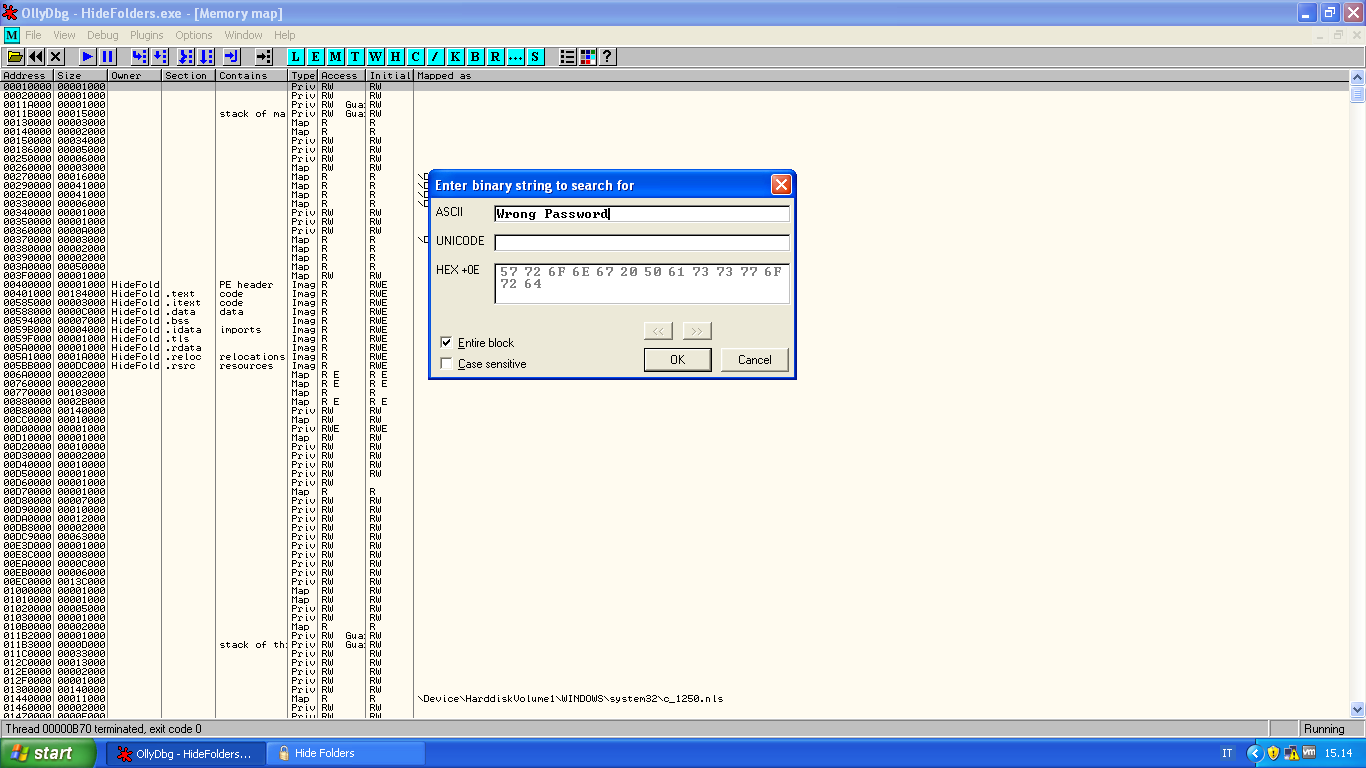
Probably this is a unicode string:
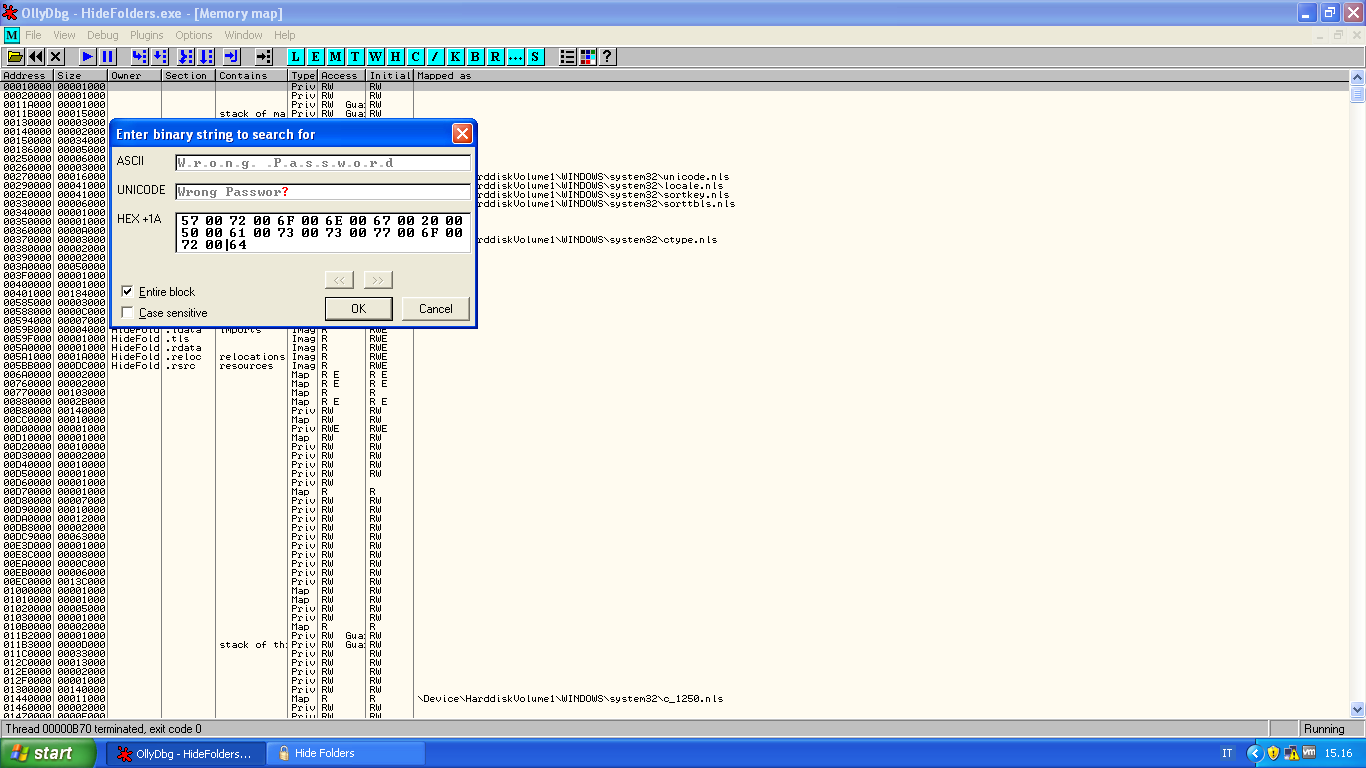
We can find the string into .itext section at address ( in my case ) 0x00587178, that will be "78 71 58 00";
Let's do another research with these bytes:
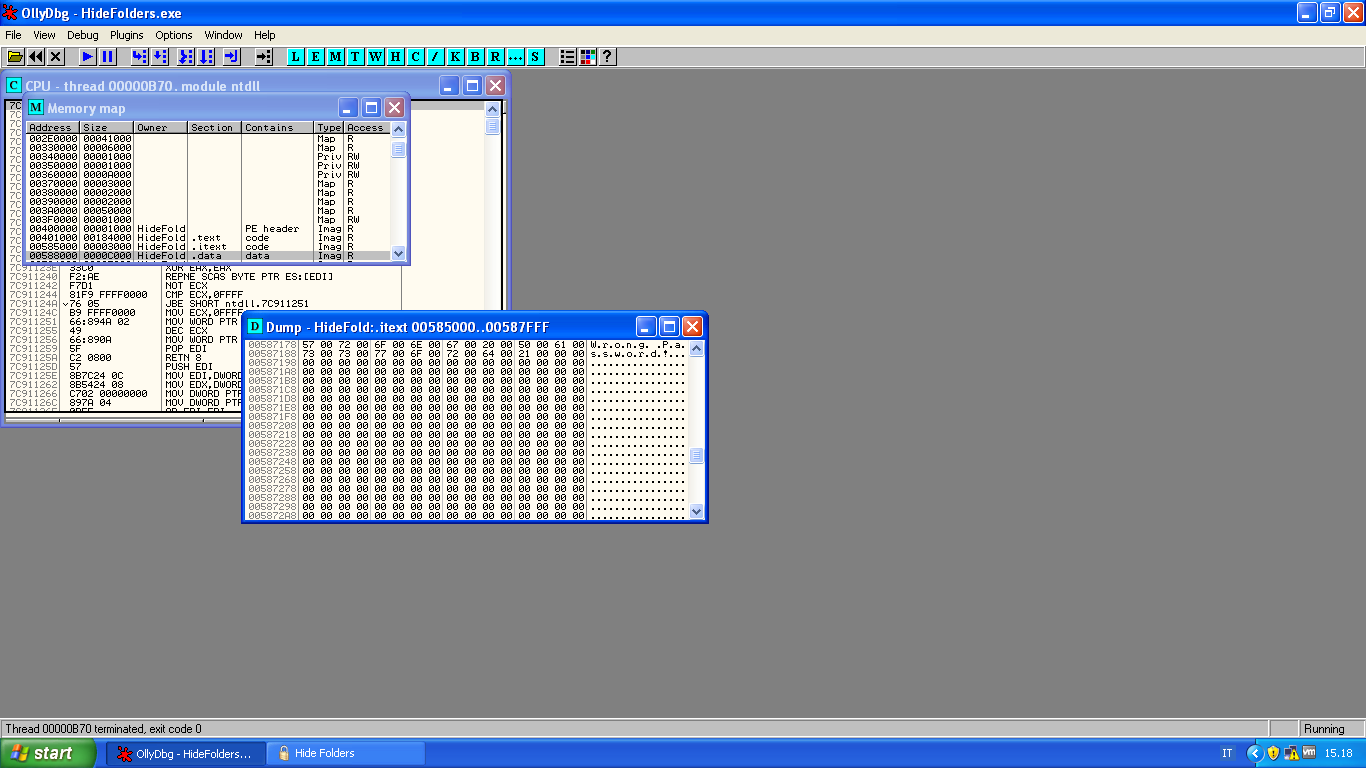
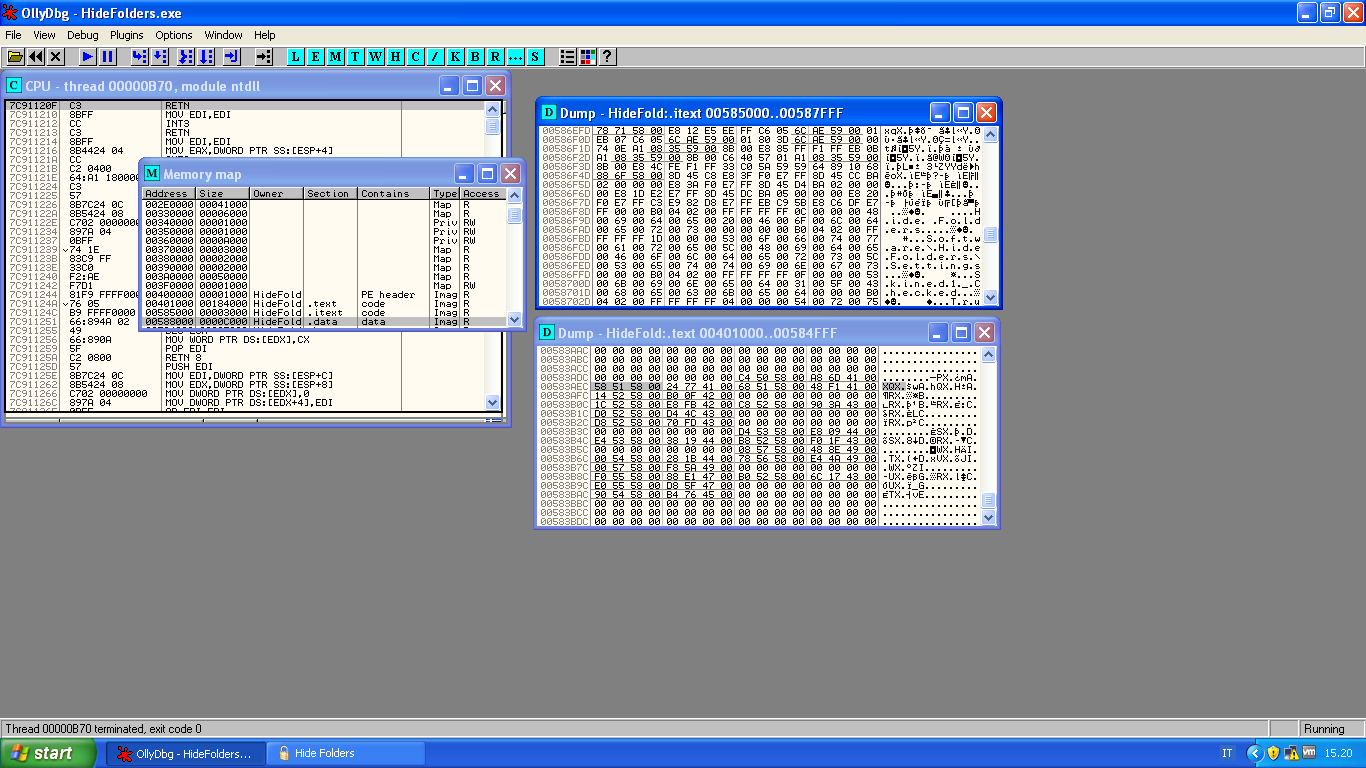
We can find these bytes into the .text and also .itext sections, let's go deep and show the disassembly of these locations.
Into the .itext at address 0x00586EFC there is an interesting instruction:
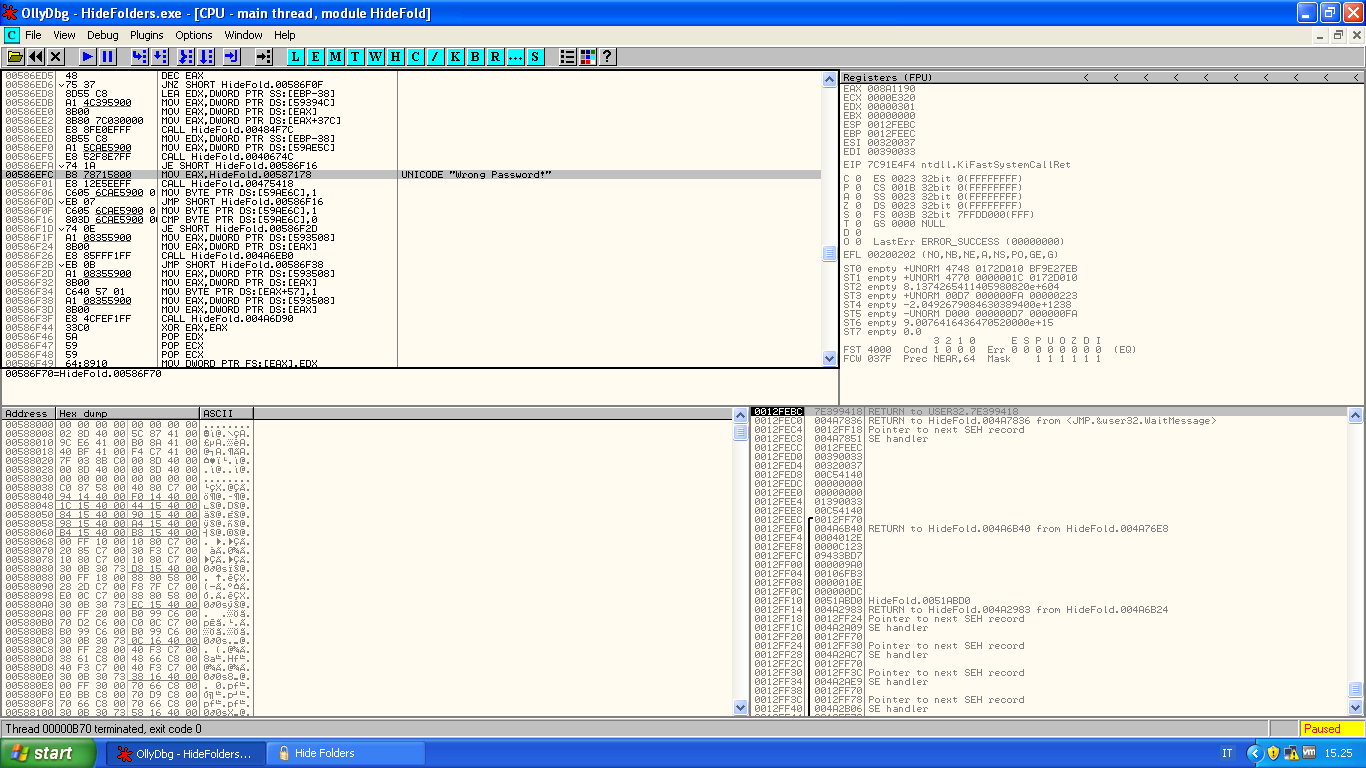
Let's place a breakpoint on the previous instruction JE; at this point type a wrong password:
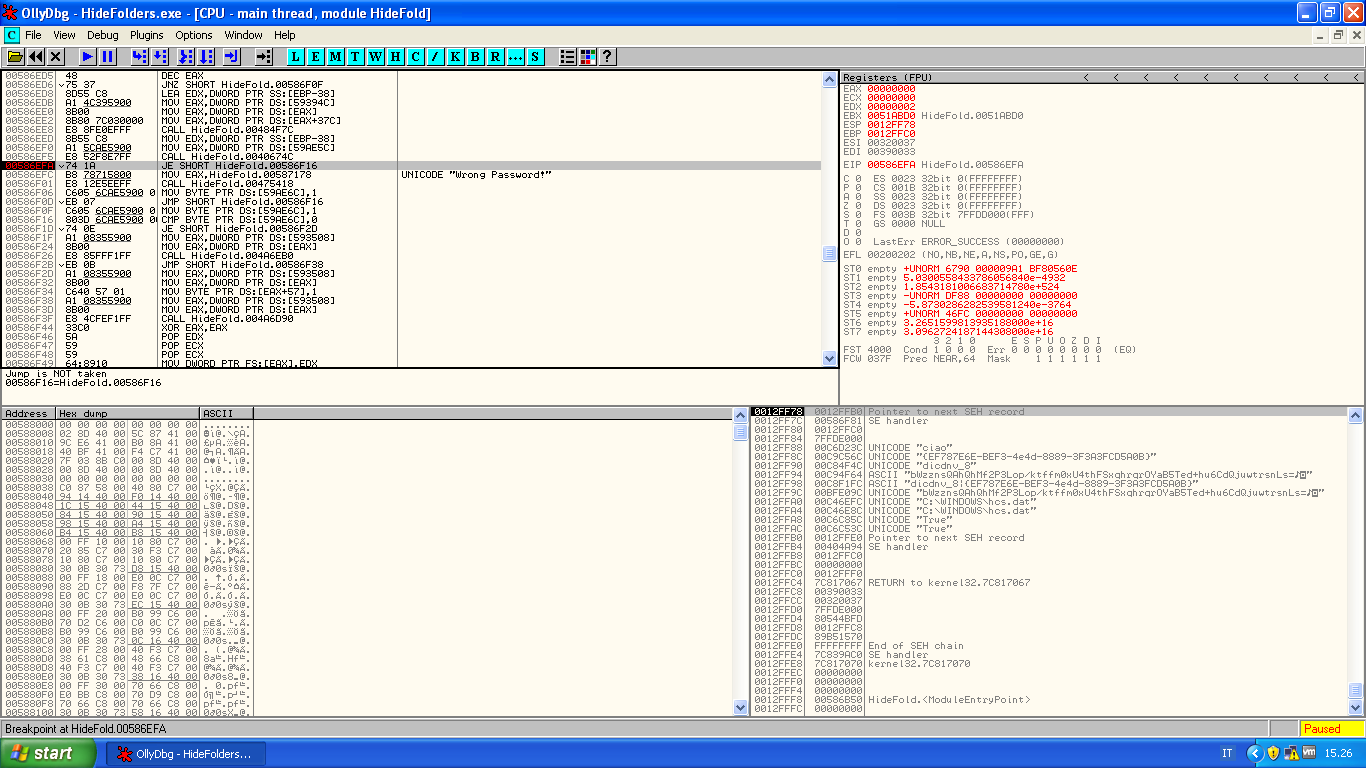
The breakpoint is immediatly reached and Ollydbg show us: "Jump is NOT taken"...so what if this instruction were JNE?
Type "SPACE" and assemble this instruction from JE to JNE...finally press Run:
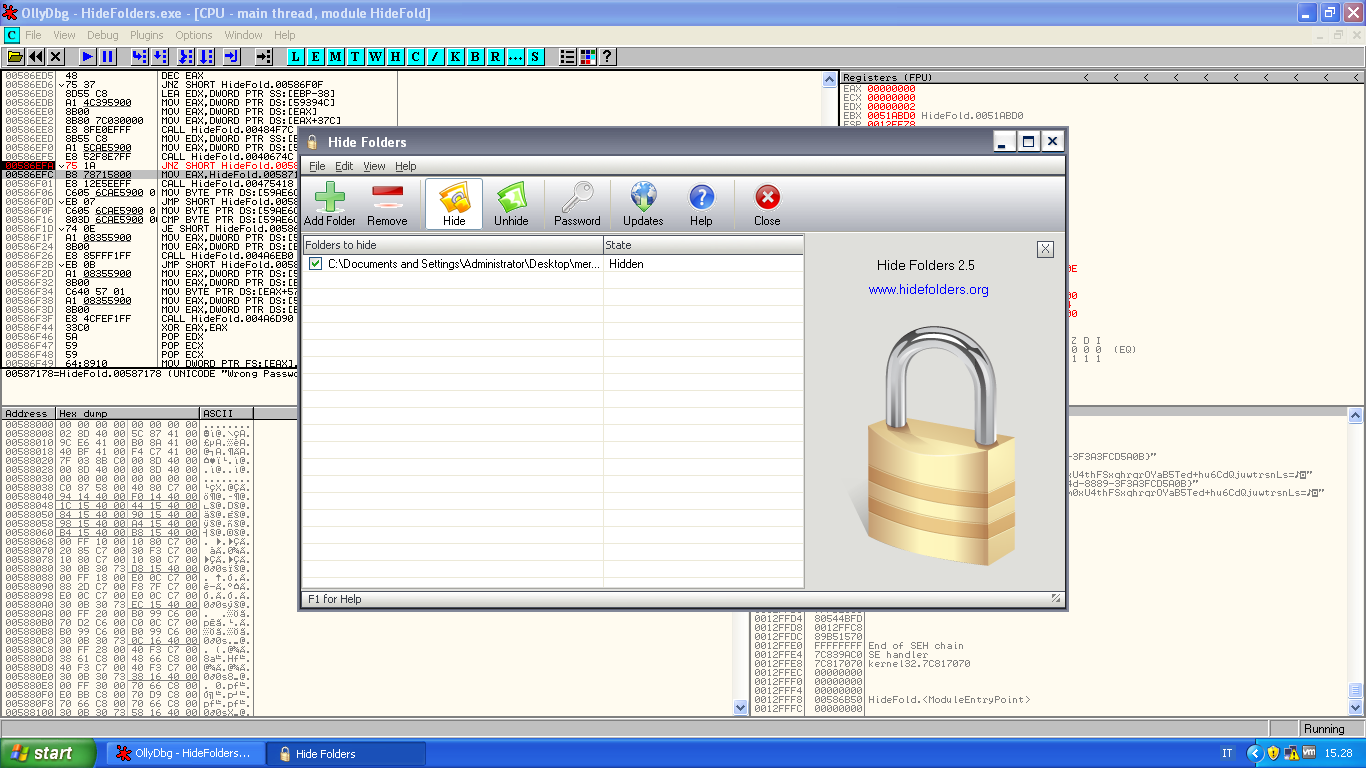
Too easy...Now you could change the forgotten Password!
Have fun :)